Security
Please bear in mind that we ask our clients to trust us with their intellectual property and information, hence we have the duty to respect and ensure the privacy and security of this information.
The trust of our customers in our professionals and services is perhaps one of our most important assets. This trust exists not only due to the services provided, but because we maintain a high standard in the way we operate.
Inappropriate use of others’ intellectual property may expose 25Friday and you to criminal and civil fines and penalties.
The following guidelines must be present and put into action in our day-to-day activities in order to guarantee best practices of security and privacy of 25Friday’s and customers’ data.
Data Classification
Our organization distinguishes the following levels of information classification:
- Public: Information of this kind can be freely distributed to anyone. E.g. company website, brochures and leaflets.
- Business confidential: Information meant to be kept internal, but no harm would be done if it falls into wrong hands. This information can be shared with team members or external parties when deemed necessary. E.g. policies and procedures.
- Confidential: The loss of confidential information can pose serious damage to the organization. E.g. financial information, strategic plans, personally identifiable information, source code.
- Secret: The loss of sensitive information can pose a threat to the persons involved and/or very serious damage to the company. In general, we strive not to have access to any secret information. This diminishes the risk in general. If secret data is collected it should be destroyed as soon as possible. E.g. special categories of personal information, access credentials to secure systems, source-code repositories and VPNs.
When no classification is given, the default is business confidential.
Work Secure
- Always think twice about the impact before you distribute or share 25Friday information. Information is only to be shared with the person(s) for whom this information is intended. Make sure that information does not end up in unwanted places or with unwanted people.
- Make sure to lock your screen whenever it is out of your line of sight.
- Whenever you receive a message for which you suspect the authenticity or origin, do not open any attachments and do not follow any links provided in that message.
- Be alert to website visits (it could be a fake, scam website). In case of doubt check the URL address and ask a colleague.
- Within the product support cycle make sure to only apply certain solutions when you have done proper authentication of the request(ee).
- Sometimes it’s necessary to call someone by phone (via their company phone number) in order to get extra validation.
- Prevent that a person sends confidential information to us (e.g. passwords) and when it happens, destroy those as soon as possible.
- Comply with the clean-desk policy. Make sure that when you leave your desk at the end of the day there is no confidential information that can be taken by third parties.
- Only software from reputable sources should be installed on devices. Discuss it with your manager when in doubt.
- Only software intended for business is allowed on 25Friday-owned laptops.
- Do not use unencrypted public Wi-Fi networks. Avoid using untrusted networks.
- Do not leave the laptop in an unattended vehicle. If you must leave your laptop in an unattended vehicle for a short period of time, always lock your laptop in the trunk of the car. A visible laptop is a target. This should also apply to your daily commute.
Data Breaches
- In case of any breach or suspected breach of data, any 25Friday employee has to report it to his/her immediate manager.
- This report should be made within two hours after discovery. This also includes events such as losing a device with business data stored on it or suspecting that a password to one of your accounts is compromised.
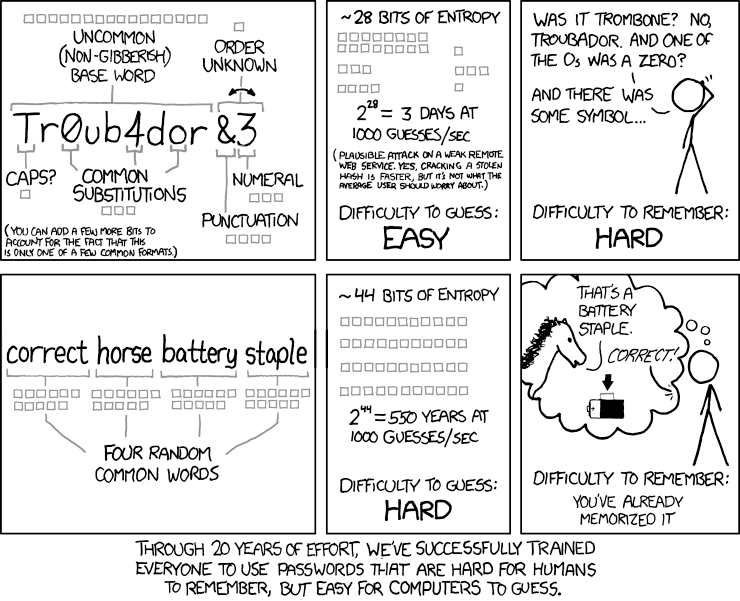
Passwords
- Passwords should be strong (at least 12 character and not on known password dictionaries);
- Do not use the same password for more than one service or system;
- Change the passwords at least once per year;
- Do not use variants of the old password (e.g. adding a number to the old password);
- As it is almost humanly impossible to remember all the different strong passwords, the use of password managers such as LastPass, 1Password or KeePass is encouraged!
- Passwords cannot be stored in insecure media such as Excel files / in-built browser password manager / post-its.
Devices and Backups
For devices carrying data labelled confidential or secret, the following extra measures apply:
- Employees are required to have mandatory backups of every data not centrally managed (e.g. on Version Control Systems, OneDrive, Confluence, …).
- Always use (full disk) encryption on laptops, mobile phones and tablets. We recommend VeraCrypt for this, but other alternatives can be used, such as Bitlocker on Windows computers or MacOS disk encryption feature for Macs.
- Delete information as soon as it is no longer applicable;
- Cloud storage accounts can only be used after prior approval of management and can only have an @25friday.com mail address as a login;
- In case you damage your device unintentionally, contact your Manager or HR Partner for further steps. Please refer to the Equipment Policy additional information.